A new phishing scam is doing the rounds and it’s targeting WordPress plugin developers. This is a very interesting attack vector, explosively damaging when successful.
Dear WordPress Plugin Developer,
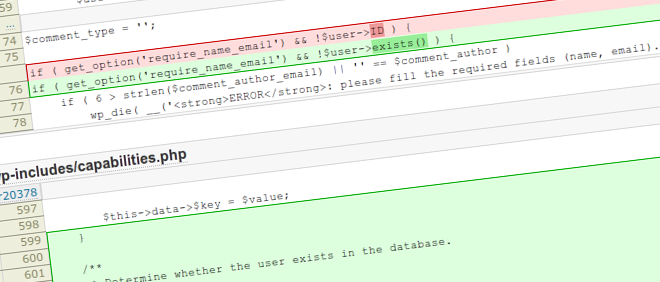
Unfortunately, a plugin you are hosting has been temporarily removed from the WordPress repository. We are going to manually review your plugin because it has been reported for violating our Terms of Service. If your plugin does not get approved then it will be permanently removed from the WordPress repository.
You can check if your plugin has been approved or rejected at
https://wordpress.org/extend/plugins/my-plugin-status/
Very unconventional, not your usual e-mail or PayPal account phishing, it’s WordPress. A little short of 20000 plugins, shared among less authors, so not a lot of victims to play with. The subsequent aim of a phishing attack appears to be the modification of plugins to inject malicious code and get WordPress installations with the plugin infected. People using the plugin would then update and bring the bad code in.
Looks quite difficult to accomplish though; it’s hard enough to get a plugin developer to not notice a fake WordPress.org site, then not smell anything funny going on even if they enter their credentials. Hmmm…
The phishing site is currently disabled (404), looks like the attack has been dismantled quite quickly and efficiently. The link https://wordpress.org/extend/plugins/my-plugin-status/ now leads to a nice plugin by the WordPress team. Well done, WordPress.org for acting quickly and efficiently.
To users of plugins, be aware of sudden updates, review code, contact the authors.
Source: Warning Phishing Attempt @ WordPress.org
Published 13 years ago
by soulseekah
with no comments
tagged phishing, scam, security in WordPress
phishing scam security WordPress