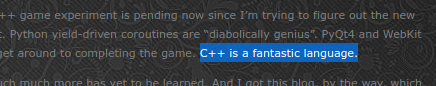
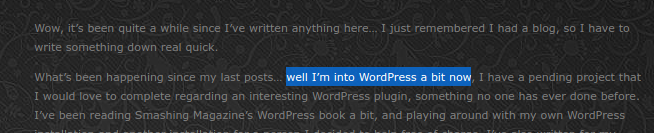
Legend has it that you can “Hire the Top 3% of Developers” over at Toptal, and I’ve actually been a member there since early 2015. I remember the onboarding process was quite serious.
Recently, I’ve been helping out screening a full-time WordPress developer for a large project involving BuddyPress, Gravity Forms and Woocommerce. I hop on very short technical calls that usually last under 15 minutes where I talk a bit about WordPress and ask some simple questions. This lets me get a feeling of whether they are competent or not.
Over the course of the last week I spoke to 4 “talented” candidates who had more than 10 years of experience with WordPress. Two of the interviews lasted for 5 minutes, the other two about 10 minutes. I asked the following questions to try and get a conversation going:
- Can you show me some code you’re written?
- What do you like about WordPress development? What don’t you like?
- What’s the difference between sanitizing and escaping in WordPress? What vulnerabilities are prevented?
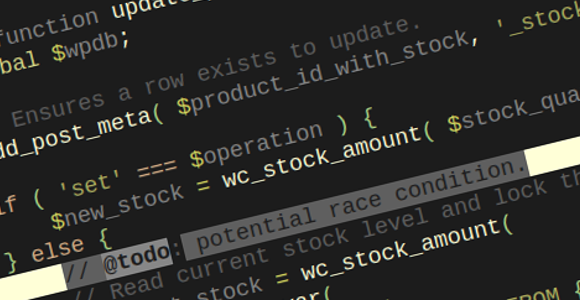
- Can you properly escape the following query
$wpdb->get_results( "SELECT * FROM $wpdb->posts WHERE post_title LIKE '%{$_POST['s']}%'" )?
- What is fragment caching and how would you implement it in WordPress?
None of the interviewees were able to sanitize the query properly, one took the liberty of trying to look up the WPDB class documentation and still failed to properly combine $wpdb->prepare and $wpdb->esc_like.
These “highly experienced” WordPress developers wanted a $120k/yr. salary (I’m sure Toptal takes a cut as well) and were unable to answer the most basic day-to-day WordPress development questions during a technical interview.
Toptal, are you sure you’re vetting these people correctly? Look at what Codeable are doing.
</rant>
Published 3 years ago
by soulseekah
with 2 comments
in General, WordPress
General WordPress