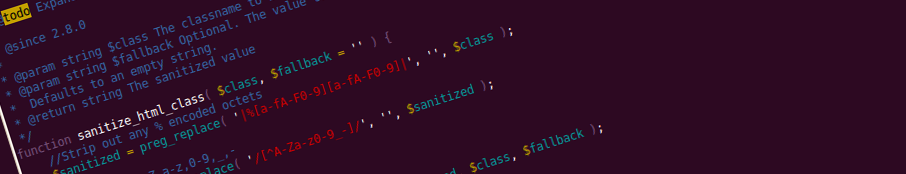
WordPress Escape Functions
The process of escaping data an important one, since the lack of thereof can lead to XSS and other naughty and unexpected things, among the legit data that just breaks specific data formats.
Consider HTML attributes. Imagine you have the following simple code:
$image_src = get_uploaded_image_src(); // not any specific function echo '<img src="' . $image_src . '" />';
What if the uploaded image is called “Horizons” by LTJ Bukem.jpg? You end up with broken HTML: <img src=""Horizons" by LTJ Bukem.jpg" />… not to worry though, WordPress comes a dozen escape functions for taking care of all these sorts of things. However, with the myriad of escaping functions provided in WordPress, it is often times difficult to remember which is which and whether there is an escape function for a specific case.